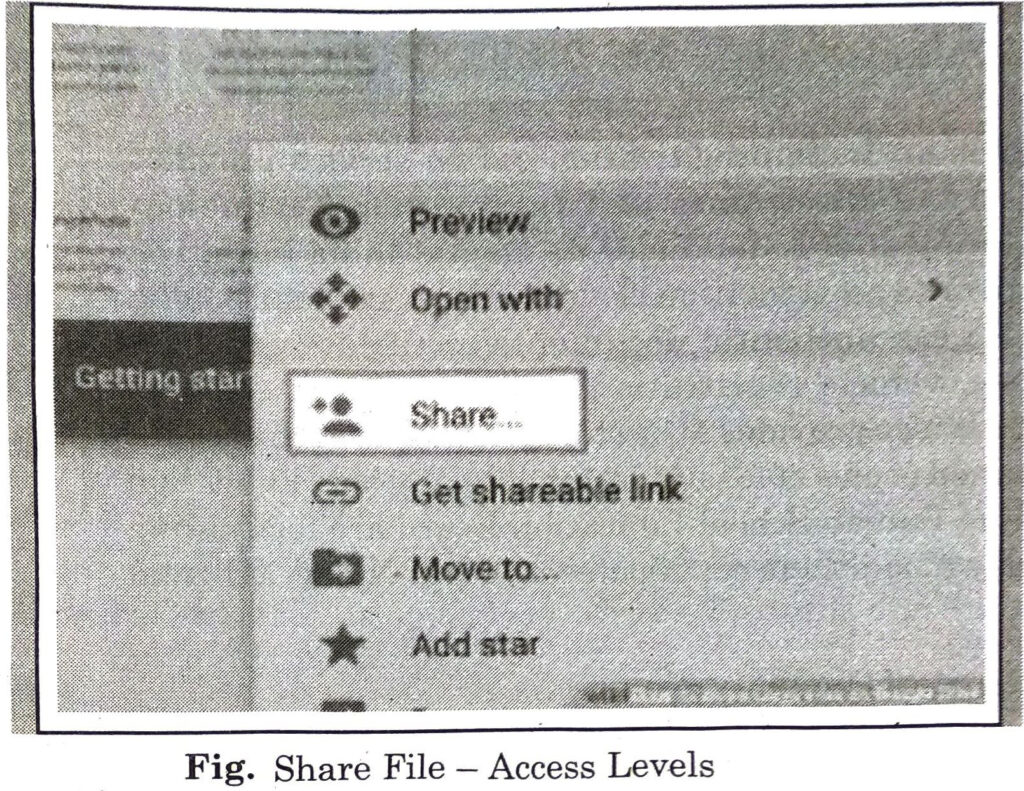
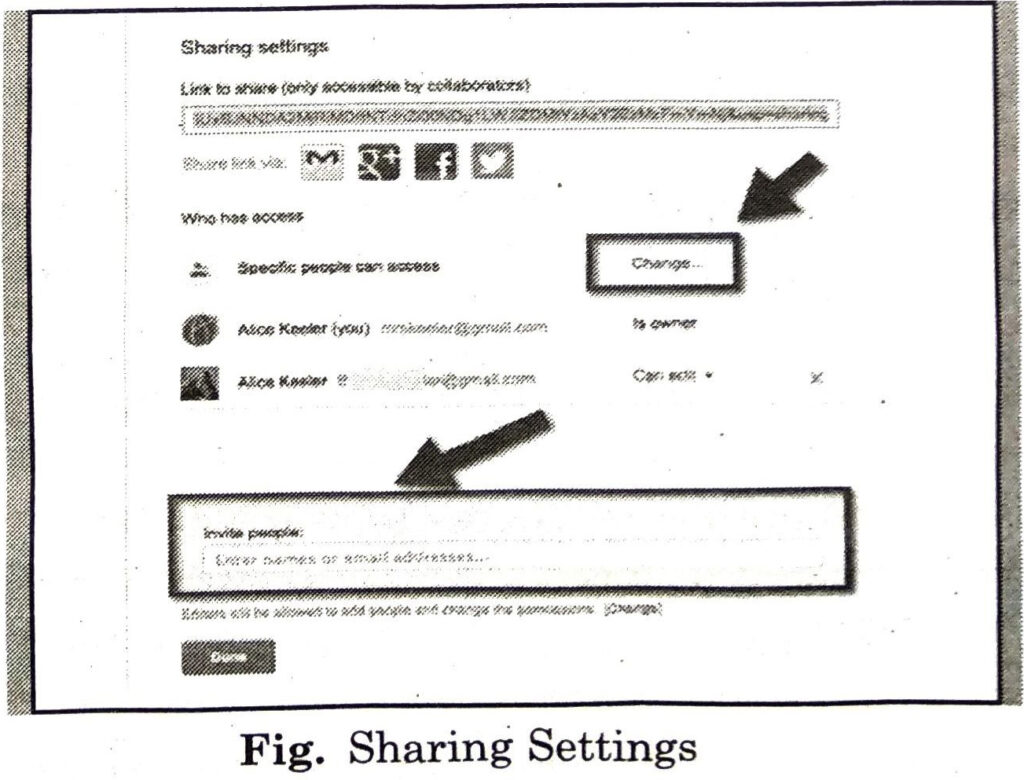
These sharing options can be :
1. Editor: Users can edit the file or folder and share it with others.
2. Commenter: Users can view and add comments to the file but can’t edit the file.
3. Viewer: Users can see the file or folder but can’t edit or comment on it.
(vi) After setting the access level, click on Send button. (The users will receive an email letting them know a file or folder has been shared with them.)
(vii) If you want to share multiple files at once, add the files to a folder in Drive and then share the entire folder with the people you want to share the files.
DIGILOCKER
DigiLocker is an Indian digitization online service provided by the Ministry of Electronics and Information Technology (MeitY), Government of India under its Digital India initiative. DigiLocker provides an account in cloud to every Aadhaar holder. It allows to access authentic documents/certificates such as driving license, vehicle registration, academic mark sheet in digital format. It also provides 1GB storage space to each account to upload scanned copies of legacy documents. Various Education Board including Punjab School Education Board are facilitating students to download their certificates of Class X and XII from DigiLocker. DigiLocker
Objectives of Digital Locker
The key objectives with which the DigiLocker was introduced by the Government of India are as follows:
(i) To enable digital empowerment among the citizens of the country.
(ii) To minimize the physical usage of documents.
(iii) To enable the feature of e-signing by making documents available electronically.
(iv) DigiLocker will increase the authenticity of documents by online upload.
(v) It will reduce the existence of fake documents.
(vi) Web portals and mobile applications are made available for easy access.
(vii) To reduce the administrative overhead of Government departments and agencies.
(viii) Residents can easily access the documents anytime and anywhere.
(ix) To facilitates sharing of documents easily.
(ix) To ensure privacy and authorized access to user’s data.
INTERNET THREATS AND SECURITY
An Internet threat is any threat that uses the Worldwide web to facilitate cybercrime. Internet threats are also known as web threats. These threats include multiple types of malware and frauds. Sources of these threats can be links sent by an email or malware attachments etc. Cyber criminals steal information for subsequent sale.
Internet Threats
Some of internet threats are as follows:
- Virus: VIRUS stands for Vital Information Resources Under Siege. A computer virus is a computer program that cause some type of damage to a computer software, hardware or data. It can also replicate itself into other computer programs. Once virus is present on a computer, it typically performs some type of harmful action, such as corrupting data or files.
- Spyware: Spyware is a malicious program. It is designed to enter our device. It collects the information from the computer and sends it to a third party without consent. Once the spyware program is installed, it starts collecting information without knowledge. Spyware often enters system when some type of free software is installed.
- Trojan horse: A trojan horse is a type of malware designed to provide unauthorized, remote access to a user’s computer. Trojan horses do not have the ability to replicate themselves like viruses. They can lead to viruses being installed on a machine. They allow the computer to be controlled by the Trojan creator. The term gets its name from the Greek story of the Trojan War. Trojan horse software operates the same way, where Trojan is our computer and the horse is the malware application.
- Phishing Scams: Phishing is an e-mail fraud method. The creator send legitimate-looking email in an attempt to gather personal and financial information in it. These messages appear to come from trustworthy sources. The message asks people to provide sensitive information, such as their login details. The message looks very official. It may contain logos and formal language.
Internet Security
Internet Security means to the software or preventive measures which are used to protect computer from the internet threats. Some of the common tools and techniques used for this purpose are :
- Anti-virus: The best way to deal with computer virus is to use antivirus software. Antivirus software helps to protect a computer system from viruses and other harmful programs. Antivirus oftware scans our online activity. It ensure not to download infected files. Antivirus software also helps to detect and remove viruses from our computer system. Some of the commonly used antivirus are Norton, Kaspersky, Avira, Avast, Mcafee etc.
- Anti-Spyware: Anti-spyware is a type of software that is effective to detect and remove unwanted spyware programs. Removing spyware can be difficult as they installs itself again when deleted. Some antivirus softwares are bundled with the spyware management tools.
- Prevention from Trojan Horse: To keep system safe from Trojan horses, never download or install software from a untrusted source. Never open an attachment or run a program received via email from unknown or untrusted ources. Make sure a Trojan antivirus is installed on computer and having a valid license.
- Prevention from Phishing Scam: Link and login should not be followed only from the official website. In order to protect yourself from these Phishing Scams.
CYBERCRIME AND CYBER ETHICS
Cybercrime
Any offenses committed against individuals or groups of individuals to harm the reputation or cause physical or mental trauma through electronic means can be defined as Cybercrime.
Cybercrime is an unlawful act wherein the computer is either a tool or a target or both. Cybercrime is a crime that involves a computer and a network. The computer may have been used to commit the crime. In many cases, it is also the target. Cybercriminals may threaten a person or a nation’s security and financial health. Cybercrimes can involve criminal activities that are traditional in nature, such as theft, fraud, forgery, defamation and mischief.
Cybercrimes are of two ways:
- Computer as a Target: The crimes in which a computer is used to attack other computers. For example: Hacking, Virus/Worm attacks, DOS attack etc.
- Computer as a Weapon : The crimes in which computer is used to commit real world crimes. For example: Cyber Terrorism, IPR violations, Credit card frauds, EFT frauds etc.
Preventive Measures Against Cybercrime
Some measures which can be taken to protect against cybercrimes are :
- The user must use a full-service internet security suite.
- The user must use strong passwords for various online websites.
- Keep your software updated.
- Keep your personal and private information locked down.
- Start with a strong encryption password as well as a virtual private network.
- You can teach your kids about acceptable use of the internet without shutting down communication channels.
- Keep yourself up to date on major security breaches.
- Take measures to protect yourself against identity theft.
- If you believe that you’ve become a victim of a cybercrime, you need to alert the local police..
Cyber Ethics
The term “cyber ethics” refers to a set of moral rules or a code of behaviour applied to the online environment. Cyber ethics refers to the code of responsible behaviour on the internet. It is to be ensured that users understand their responsibilities for conducting themselves online. Cyber ethics refers to the basic ethics and etiquette that must be followed while using a computer system. Ethics, in general, refers to propagating good behaviour, similarly by cyber ethics we refer to propagating good behaviour online that is not harsh or rude. Cyber ethics governs rules that individuals must be polite and responsible when they use the internet. Cyber ethics aim to protect the moral, financial, social behaviour of individuals. Cyber ethics engages the users to use the internet safely and use technology responsibly and sensibly.
Principles of Cyber Ethics
Don’ts
(i) Do not use a computer to cause harm to other people.
(ii) Do not interfere with other people’s computer work.
(iii) Do not snoop around in other people’s computer files.
(iv) Do not use a computer to steal unauthorized information.
(v) Do not copy or use proprietary software for which you have not paid.
(vi) Do not use other people’s computer resources without proper authorization.
Do’s
(i) Do think about the social consequences of the act that you are doing online.
(ii) Do always use a computer in ways that ensure respect for your fellow humans.
Computer Guide for Class 9 PSEB Internet Applications Textbook Questions and Answers
Multiple Choice Questions :
1. ‘Gmail’ is a free email service provided by ………..
(A) Yahoo
(B) Google
(C) Rediff mail
(D) Hotmail.
Ans. (B) Google
2. A …….. is a type of test used in computing to determine whether or not the user is human.
(A) CAPTCHA
(B) DERTSA
(C) HEPTCHA
(D) NEPHCA.
Ans. (A) CAPTCHA
3. ……………… is a type of malware designed to provide unauthorized, remote access to a user’s computer.
(A) Spyware
(B) Trojan
(C) Malware
(D) None of these.
Ans. (B) Trojan
4. ……………. is a computer program that replicates itself into other computer programs.
(A) Spyware
(B) Virus
(C) Phishing
(D) Malware.
Ans. (B) Virus
5. …………………. is an Indian digitization online service provided by the Ministry of Electronics and Information Technology (MeitY), Government of India under its Digital India initiative.
(A) DigiLocker
(B) DigiProgram
(C) DigiHacker
(D) DigiBanker.
Ans. (A) DigiLocker
Write True/False :
1. Spyware is an e-mail fraud method in which the wrongdoer sends out legitimate looking email in an attempt to gather personal and financial information from recipients.
Ans. False
2. Google Drive does not allow us to store and share files online.
Ans. False
3. The best way to deal with the threat of a computer virus is to use antivirus software.
Ans. True
4. The Web threat is any threat that uses the World Wide Web to facilitate cybercrime.
Ans. True
5. Google Meet is a video conferencing service by Google.
Ans. True
Short Answer Type Questions :
Q. 1. Define E-mail.
Ans. Email is a way of sending electronic messages or data from one computer user to one or more recipients.
Electronic Mail (e-mail) is one of the most widely used services of Internet. This service allows an internet user to send a message in formatted manner (mail) to the other internet user in any part of world. Message in mail not only contain text, but it also contains images, audio and videos data. The person who is sending mail is called sender and person who receives mail is called recipient. It is just like postal mail service.
Q. 2. Give the names of any four Google apps.
Ans. Four google apps are :
(i) Google Docs
(ii) Google Sheets
(iii) Google Slides
(iv) Google Maps
Q. 3. Define Cyber Ethics.
Ans. “Cyber ethics” refers to a set of moral rules or a code of behaviour applied to the online environment. Cyber ethics refers to the code of responsible behaviour on the internet. It is to be ensured that users understand their responsibilities for conducting themselves online. Cyber ethics refers to the basic ethics and etiquette that must be followed while using a computer system.
Q. 4. What is DigiLocker?
Ans. DigiLocker is an Indian digitization online service provided by the Ministry of Electronics and Information Technology (MeitY), Government of India under its Digital India initiative. DigiLocker provides an account in cloud to every Aadhaar holder. It allows to access authentic documents/certificates such as driving license, vehicle registration, academic mark sheet in digital format.
Q. 5. What is Cloud Printing ?
Ans. Cloud Printing is the process to print documents and other materials on any device associated with the network. The devices like computers, laptops, tablets, phones etc. can be connected to a particular printer. Anything can be printed from a computer connected to that network.
Long Answer Type Questions :
Q. 1. What are Google Apps? Explain any two Google Apps.
Ans. Google Apps is a collection of Web-based applications from Google that includes e-mail, calendar, word proce-ssing, spreadsheet, maps, drive and presentations.
(i) Google Calendar is a time-management web application and mobile app. Multiple calendars can be created in it. Each calendar can be shared, with specific people or everyone. Google Calendar allows users to create and edit events. Events can have a start time and stop time. It also provides option for an “All-day event”. Reminders can be enabled for events.
(ii) Google Maps is a web mapping service. It offers satellite imagery, directions, street maps, 360° street view, real-time traffic conditions, and route planning for travelling by foot, car, two-wheeler or public transportation. Google Maps for Android and iOS was released in September 2008 having features GPS. This app is very helpful to travellers across the world.
Q. 2. What is Google Drive ? Write various benefits of Google Drive.
Ans. Google Drive allows to store and share files online. It is online storage space provided by Google. The service was launched on April 24, 2012 and provides 15 GB of free storage. Additional storage can be purchased for a monthly fee. It can be used similar to windows explorer by using web browser.
Benefits of Google Drive are discussed as following:
- Google Drive allows to send large files over internet to any person having Gmail account.
- Google Drive allows to access files remotely.
- With Drive, all our files become available on the web.
- Google Drive has its mobile application which gives us access to our files on our iPhone or smartphone.
- Google Drive has an efficient built-in search engine which allows to find content easily.
- Files can be seen by owner or by file type.
- Google Drive also have an optical character recognition function. It allows to search for words or expressions in scanned documents. It can also convert pdf or images to text.
Q. 3. Write about various methods of Internet Security.
Ans. Some of the common tools and techniques used for this purpose are :
- Anti-virus: The best way to deal with computer virus is to use antivirus software. Antivirus software helps to protect a computer system from viruses and other harmful programs. Antivirus software scans our online activity. It ensure not to download infected files. Antivirus software also helps to detect and remove viruses from our computer system. Some of the commonly used antivirus are Norton, Kaspersky, Avira, Avast, Mcafee etc.
- Anti-Spyware: Anti-spyware is a type of software that is effective to detect and remove unwanted spyware programs. Removing spyware can be difficult as they installs itself again when deleted. Some antivirus softwares are bundled with the spyware management tools.
- Prevention from Trojan Horse: To keep system safe from Trojan horses, never download or install software from a untrusted source. Never open an attachment or run a program received via email from unknown or untrusted sources. Make sure a Trojan antivirus is installed on computer and having a valid license.
- Prevention from Phishing Scam: Link and login should not be followed only from the official website. In order to protect yourself from these Phishing Scams.
Q. 4. What is Cybercrime? Write various preventive measures against Cybercrimes.
Ans. Cybercrime is an unlawful act wherein the computer is either a tool or a target or both. Cybercrime is a crime that involves a computer and a network. The computer may have been used to commit the crime. In many cases, it is also the target. Cybercriminals may threaten a person or a nation’s security and financial health. Cyber-crimes can involve criminal activities that are traditional in nature, such as theft, fraud, forgery, defamation and mischief.
Cybercrimes are of two ways:
Computer as a Target: The crimes in which a computer is used to attack other computers. For example: Hacking, Virus/Worm attacks, DOS attack etc. Computer as a Weapon : The crimes in which computer is used to commit real world crimes. For example: Cyber Terrorism, IPR violations, Credit card frauds, EFT frauds etc.
Preventive Measures Against Cybercrime :
Some measures which can be taken to protect against cybercrimes are :
- The user must use a full-service internet security suite.
- The user must use strong passwords for various online websites.
- Keep your software updated.
- Keep your personal and private information locked down.
- Start with a strong encryption password as well as a virtual private network.
- You can teach your kids about acceptable use of the internet without shutting down communication channels.
- Keep yourself up to date on major security breaches.
- Take measures to protect yourself against identity theft.
- If you believe that you’ve become a victim of a cybercrime, you need to alert the local police.
PSEB 9th Class Computer Guide Internet Applications Important Questions and Answers
Fill in the Blanks
1. ‘Gmail’ is a free email service provided by …………………….
(A) Yahoo
(B) Google
(C) Rediffmail
(D) Hotmail.
Ans. (A) Yahoo
2. Every machine on the Internet has a unique number assigned to it, called an ……………..
(A) Address
(B) E-mail
(C) ID
(D) Unique IP Address.
Ans. (D) Unique IP Address.
3. A ……………… is a type of test used in computing to determine whether or not the user is human.
(A) CAPTCHA
(B) DERTSA
(C) HEPTCHA
(D) NEPHCA.
Ans. (A) CAPTCHA
4. ………… is a type of malware designed to provide unauthorized, remote access to a user’s computer.
(A) Spyware
(B) Trojan
(C) Malware
(D) Horse.
Ans. (C) Malware
5. TV and radio on the Internet are examples of ……………… media.
(A) Streaming
(B) Limited
(C) Online
(D) Offline.
Ans. (A) Streaming
6. Gmail, yahoomail, Hotmail etc. are ……….. .
(A) google
(B) Microsoft
(C) e-mail
(D) Skymail.
Ans. (C) e-mail
7. play store is product of ……….. .
(A) Microsoft
(B) Play store
(C) Play
(D) Google.
Ans. (D) Google.
8. Files can be shared with ………………. .
(A) Hotmail
(B) Play store
(C) Google Drive
(D) Virus.
Ans. (C) Google Drive
9. ……… cures …………. .
(A) Antivirus, virus
(B) Google, Yahoo
(C) E-mail, virus
(D) Antivirus, server.
Ans. (A) Antivirus, virus
Write True/False
1. Phishing is an e-mail fraud method in which the wrongdoer sends out legitimate-looking email in an attempt to gather personal and financial information from recipients.
Ans. True
2. In BCC we type the addresses of people we want to send a copy of the mail to, without the other recipients knowing.
Ans. True
3. Digital signatures are created and verified by means of biography.
Ans. False
4. Gmail is a product of Microsoft.
Ans. False
5. We can share files on internet.
Ans. True
6. Data is not destroyed on Google Drive.
Ans. True
7. Cloud means Air clouds in computer terminology.
Ans. False
Short Answer Type Questions :
Q. 1. What is a CAPTCHA code ?
Ans. CAPTCHA Short for completely automated public turing test to tell computers and humans apart. It is a technique used by a computer to tell if it is interacting with a human or another computer.
Q. 2. What do you mean by Google Apps?
Ans. Google Apps is a package of cloud-based services that can provide your company or school with a whole new way to work together online-not just using email and chat, but over video conferences, social media, real-time document collaborations, and more.
Q. 3. What is Digital Signature ?
Ans. Digital signatures are the public-key primitives of message authentication. In the physical world, it is common to use handwritten signatures on handwritten or typed messages.
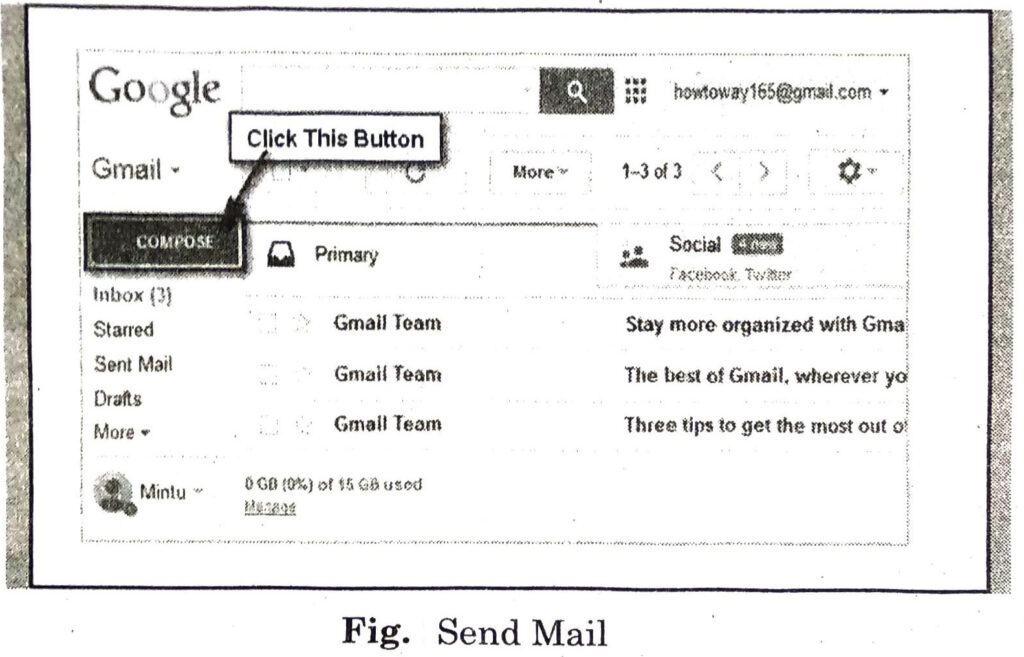
Q. 4. Write the process of sending an e-mail.
Ans. Different steps to send and receive mail are :
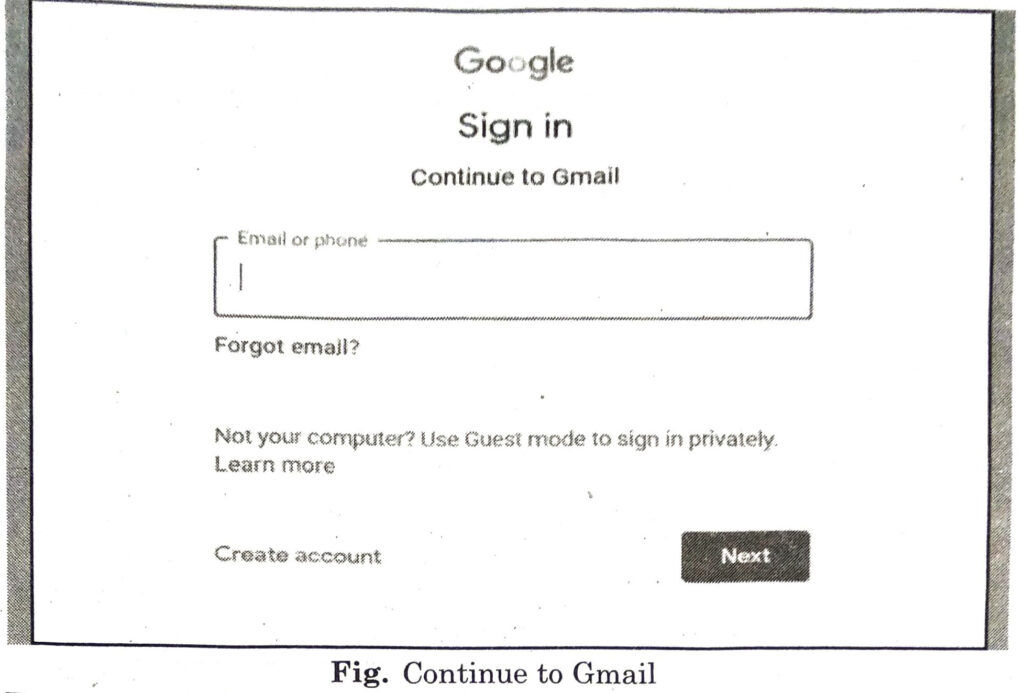
(i) Open your Gmail account by clicking on the Gmail link on the Google search page.
(ii) Click the button labeled ‘Compose’.
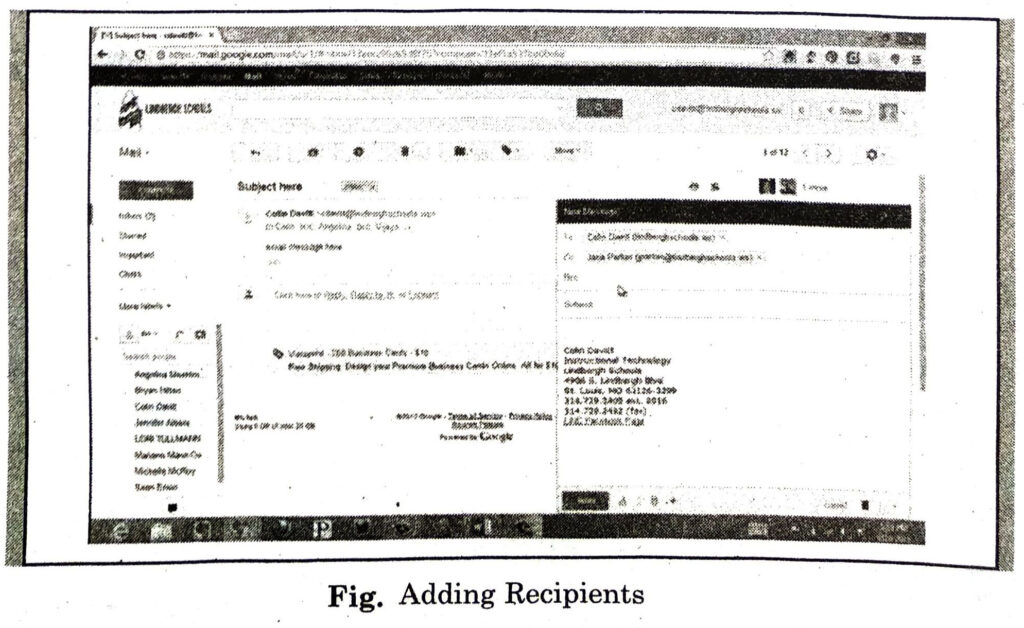
(iii) Go to the To: box. In the To: box type in the email address of the person you would like to send an email to. If there are multiple people you want to send it to, click on the Add Cc and Add Bcc buttons.
(iv) Type the email subject. The subject lets people know what the email is going to be about.
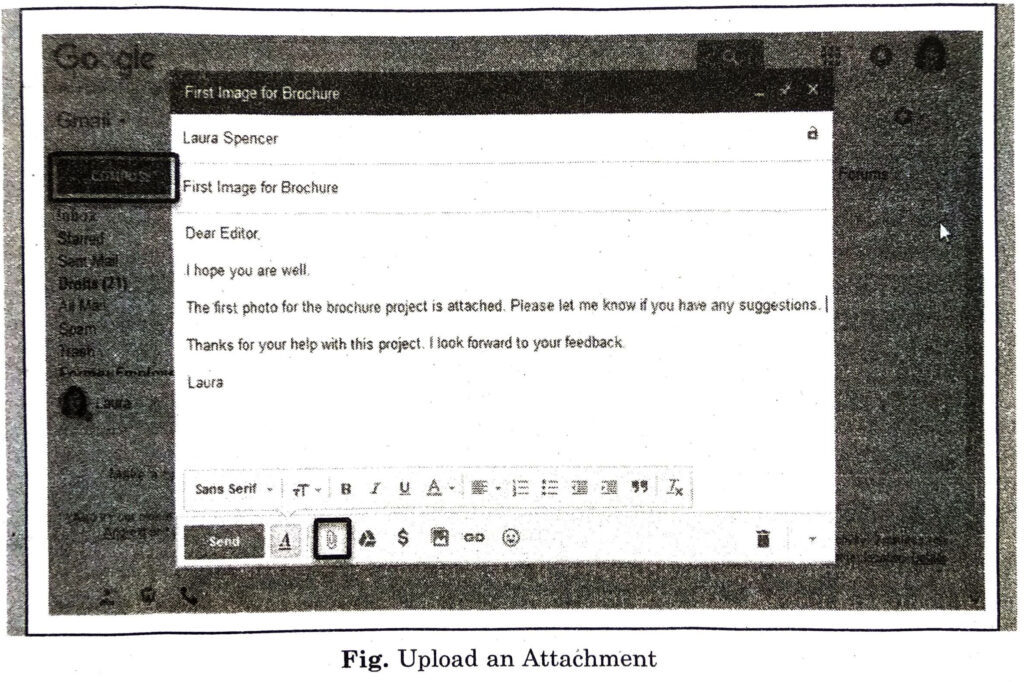
(v) Type your message in the big box below the subject box.
(vi) Click the send button below the message box.
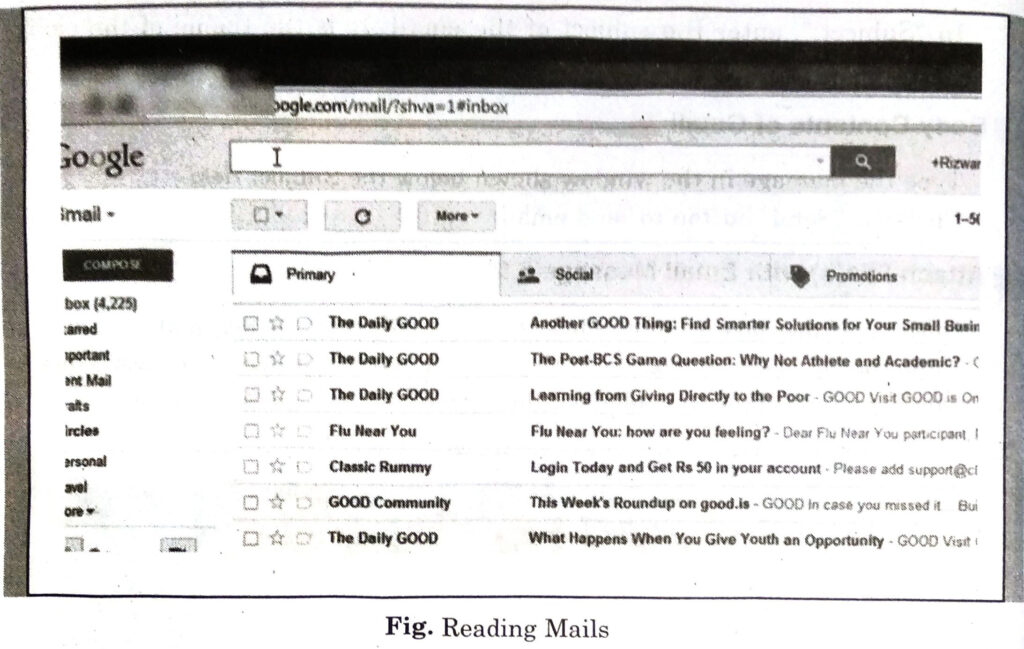
(vii) Wait until the person you sent the email replies.
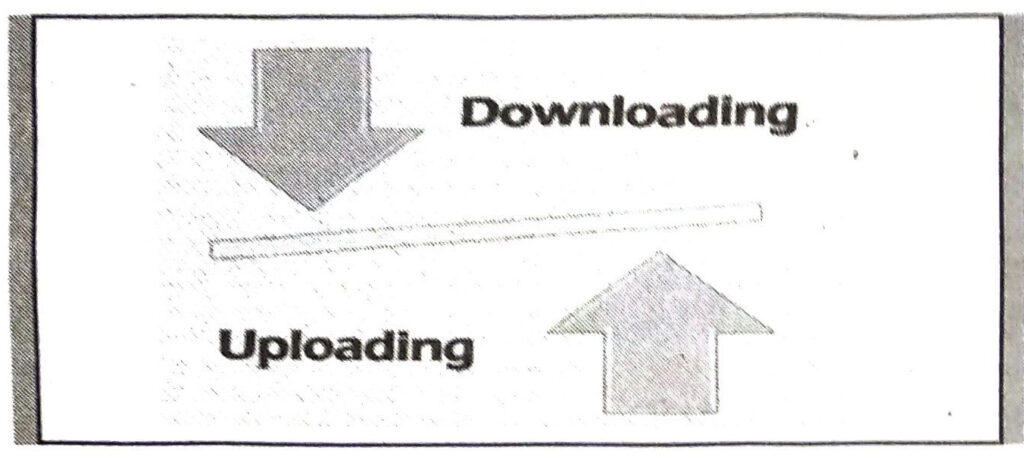
Q. 5. Write the basic steps of downloading.
Ans. Follow these steps for downloading software, games or any other files from the Internet if you use a PC running Windows XP, Vista or Windows 7.
(i) If you don’t already have one, create a Temporary Files folder by opening Windows Explorer, highlighting your hard drive (typically the c: drive), then selecting File/New/Folder. When the folder appears, name it Temp files.
(ii) Once you locate the software you want to download, click on the link to begin the download process.
(iii) First you will be asked if you want to save the file. Click the Save button, then locate the Temp file folder on your hard drive and double-click to open it. Next, click the Save button.
(iv) You can watch the file as it downloads.
Q. 6. What is Gmail?
Ans. ‘Google Mail’ or ‘Gmail’ is a free email service provided by Google. Gmail is like any other web-based email service. It can be used to send or receive emails, block spam, create an address book, and perform other basic email tasks. It has some more unique features. It is one of the most popular email services on the Web.
Q. 7. What is Cloud ?
Ans. The term Cloud refers to a Network or Internet. It can be said that Cloud is something, which is present at remote location. Cloud or network can provide services over public and private networks, i.e., WAN, LAN or VPN. Applications such as email, web conferencing, customer relationship management (CRM) run on cloud.
Q. 8. What is cloud Networking?
Ans. Cloud Networking : Cloud networking refers to hosting or using some or all network resources and services-virtual rou-ters, bandwidth, virtual firewalls, or network mana- gement software from the cloud, whether public, private, or hybrid.